📄Research Article │ 🔍Refereed │🔓Open Access
Counter-Mapping Surveillance:
A Critical Cartography of Mass Surveillance Technology After Snowden
│ │
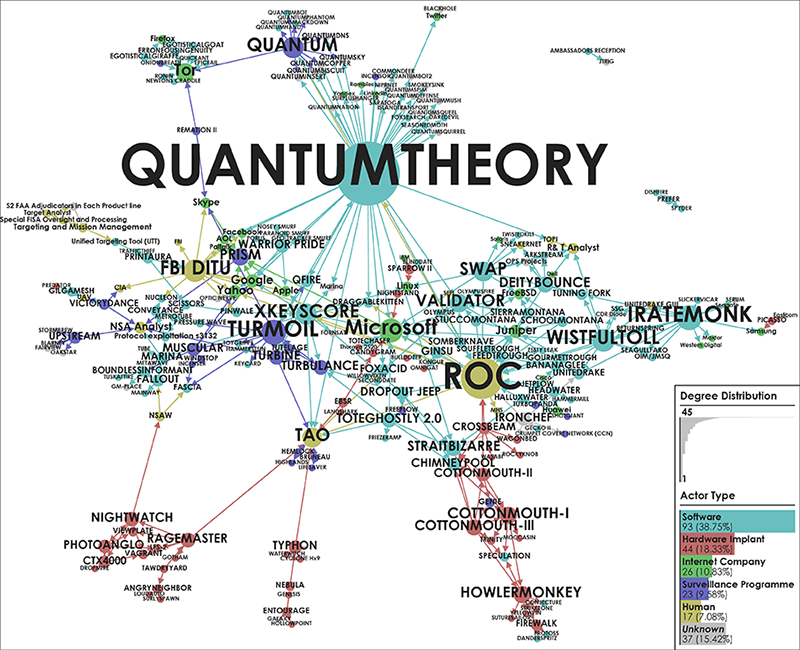
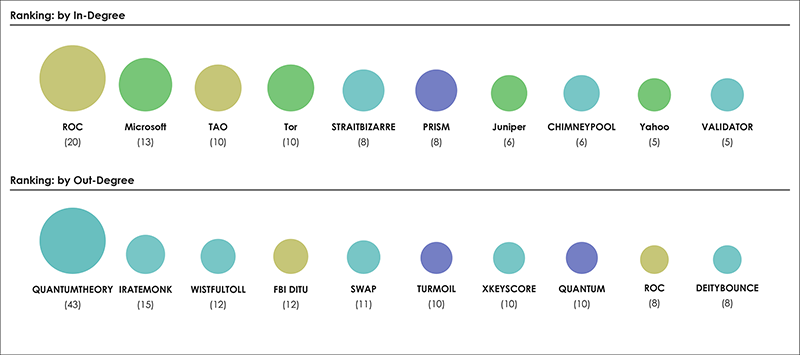
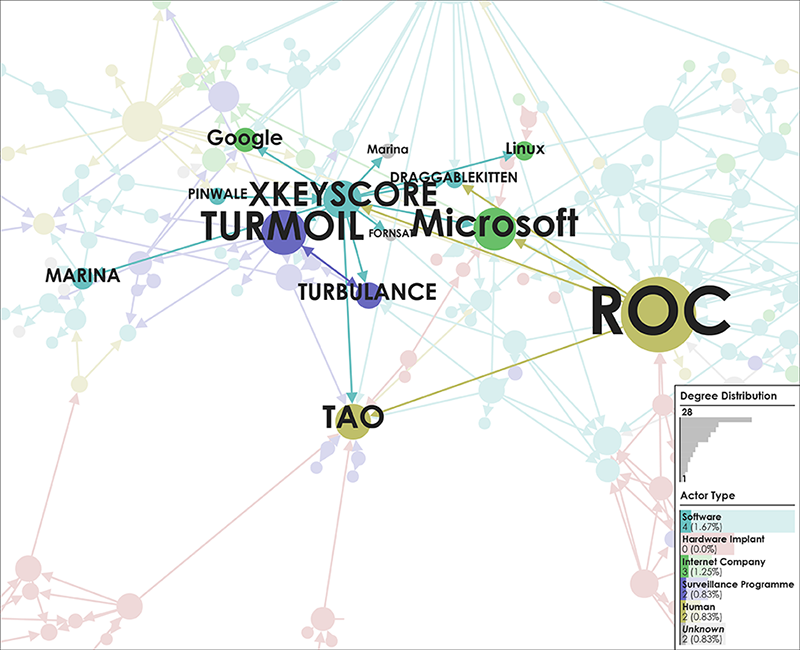
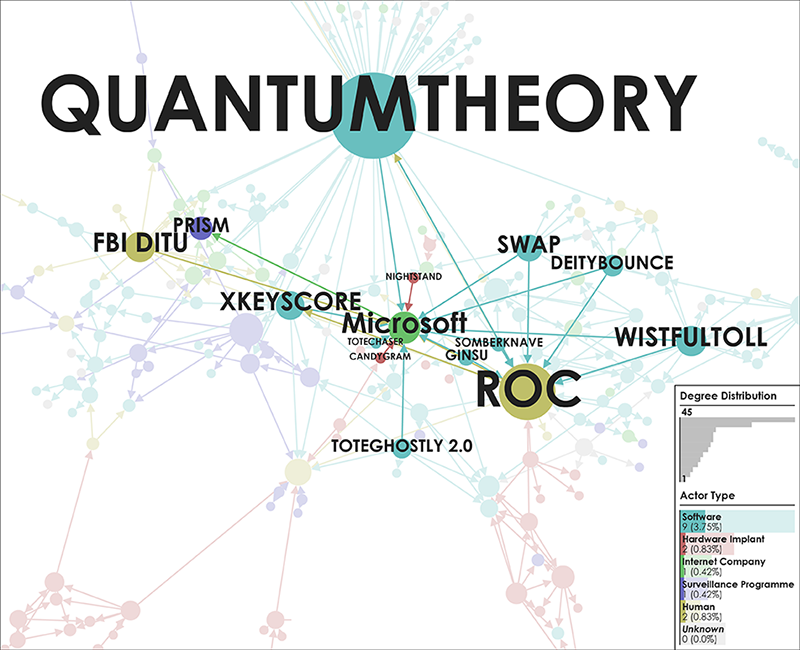
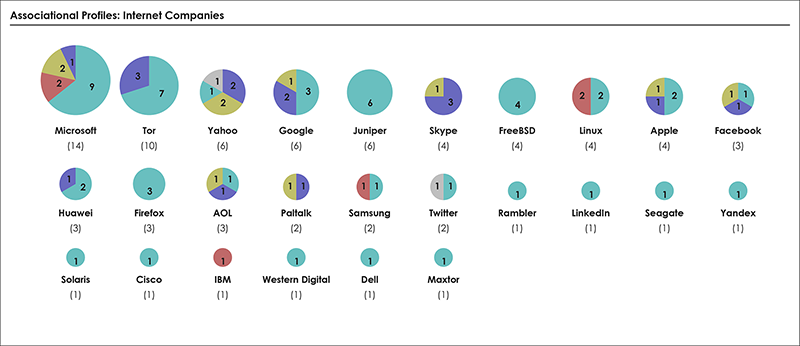
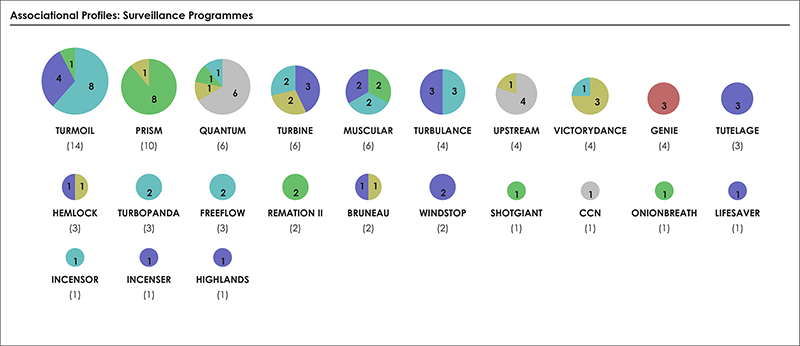
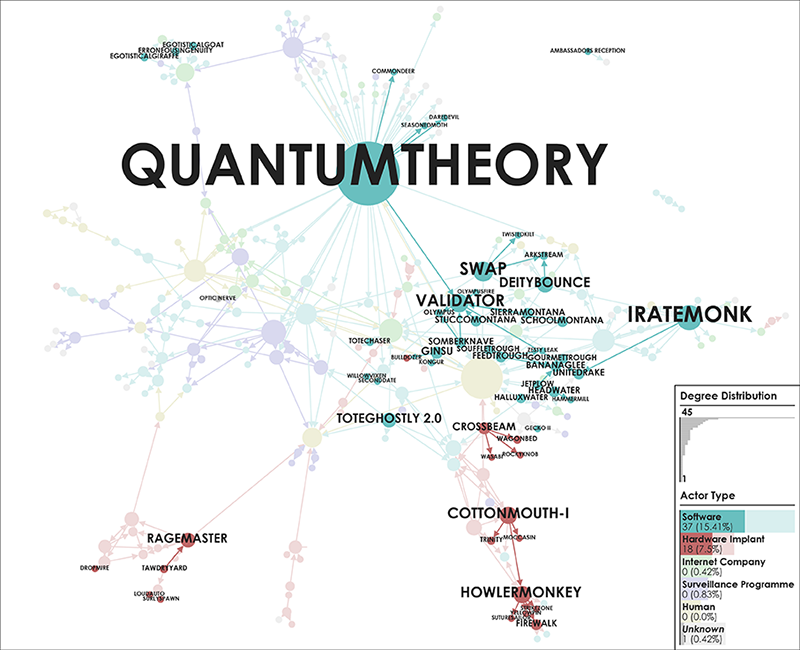
📂Edward Snowden’s Global Surveillance Revelations This article critically examines mass surveillance technology revealed by Snowden’s disclosures. It addresses that we do not only live in a society where surveillance is deeply inscribed but more urgently, that it is increasingly difficult to study surveillance when its technologies and practices are difficult to distinguish from everyday routines. Considerably, many of the technologies and systems utilised for surveillance purposes were not originally designed as proper surveillance technologies. Instead, they have effectively become surveillance technologies by being enrolled into a particular surveillant assemblage. Three contributions are made towards critical scholarship on surveillance, intelligence, and security. First, a novel empirical cartographic methodology is developed that employs the vocabularies of assemblages and actor–networks. Second, this methodology is applied to critically examine global mass surveillance according to Snowden. Multiple leaked data sources have been utilised to trace actors, their associations amongst each other, and to create several graphical maps and diagrams. These maps provide insights into actor types and dependence relations described in the original disclosed documents. Third, the analytical value of three ordering concepts as well as the logistics of surveillance are explored via notable actors and actor groups. In short, this contribution provides empirical cartographic methods, concepts, and analytical targets for critically examining surveillance technology and its particular compositions. It addresses challenges of resisting mass surveillance and some forms of data activism, and calls for the continuing proliferation of counter-maps to facilitate grounded critique, to raise awareness, and to gain a foothold for meaningful resistance against mass surveillance.
🏷mass surveillance 🏷critical cartography 🏷actor–network theory 🏷advanced networking technology 🏷global surveillant assemblage 🏷Snowden
ℹNote: This article is part of Surveillance and Security Intelligence after Snowden (cont’d), a special issue of Surveillance & Society edited by D. M. Wood and S. Wright.
📋 ✍Cite
| 📋Cite (APA) | van der Vlist, F. N. (2017). Counter-Mapping Surveillance: A Critical Cartography of Mass Surveillance Technology After Snowden. In D. M. Wood & S. T. Wright (Eds.), Surveillance and Security Intelligence after Snowden (Special Issue, Cont’d), Surveillance & Society, 15(1), 137–157. Surveillance Studies Network. DOI: 10.24908/ss.v15i1.5307. |
|---|---|
| 🔗Link (DOI) | https://doi.org/10.24908/ss.v15i1.5307 |
| Kind | Special Journal Issue; Journal Article; Original Research Article |
|---|---|
| Author | F. N. van der Vlist |
| Designer | F. N. van der Vlist |
| Publication Date | 2017, February 28 |
| Journal | Surveillance & Society (S&S) |
| Volume | 15 |
| Issue | 1 |
| Section | Surveillance and Security Intelligence after Snowden (cont’d) |
| Editor (Section) | D. M. Wood; S. Wright |
| Pages | 137–157 (31) |
| Publisher | Surveillance Studies Network |
| Identifier | 10.24908/ss.v15i1.5307 [self]; https://ojs.library.queensu.ca/index.php/surveillance-and-society/issue/view/Race [part of]; 1477-7487 [part of] |
| License | CC BY-NC-ND 4.0 |
🖇Attached ⋮
| 🖇Attached | Name | 🕓Date Modified ↧ | Kind | Access | |
|---|---|---|---|---|---|
| ↩ | [Parent Directory] |